That innocent Chrome Remote Desktop app sitting dormant on your computer? It’s basically a master key to your entire digital life. This deceptively simple Google tool grants complete control over any machine it touches—and you probably forgot it was even installed.
How This Actually Works
Chrome Remote Desktop’s simplicity masks a serious security vulnerability.
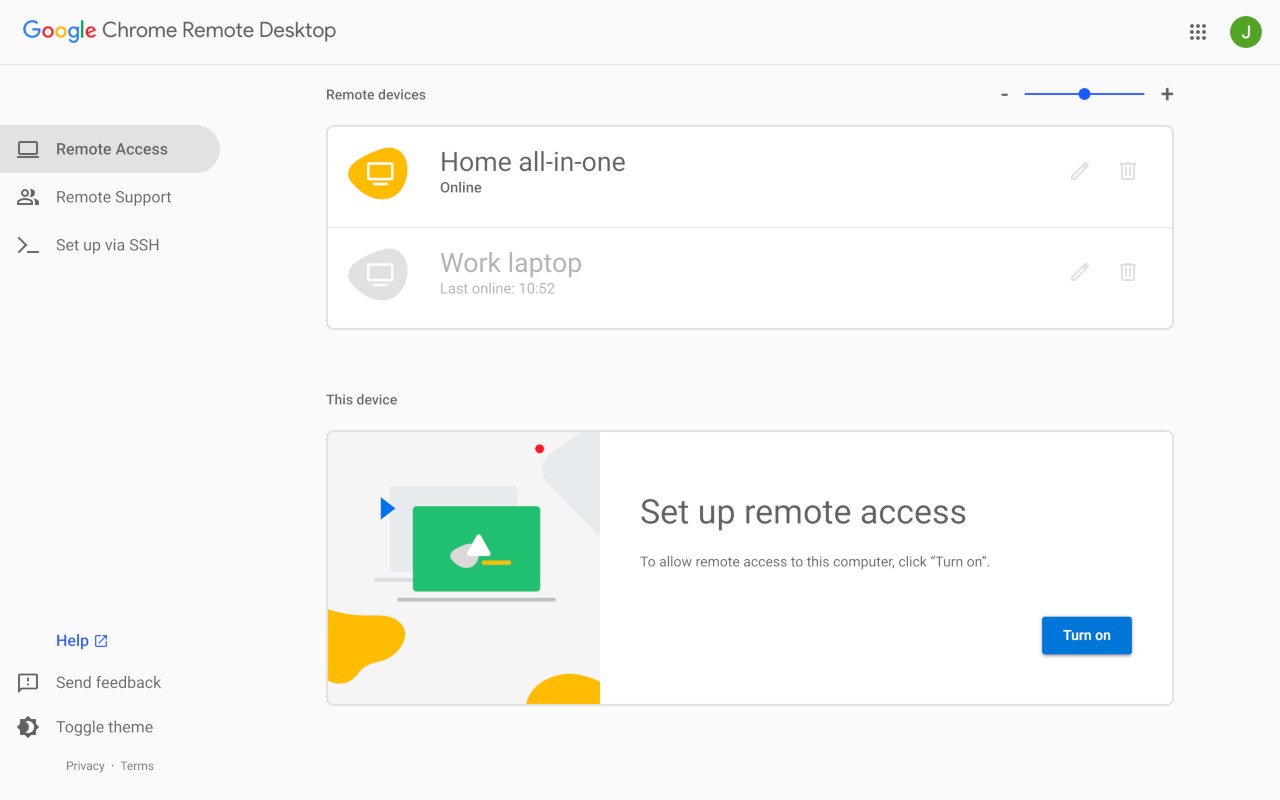
Setting up Chrome Remote Desktop feels refreshingly straightforward in our overcomplicated tech world. Log into your Google account on both devices, generate a PIN for the host machine, and boom—you’re remotely controlling computers across continents. The connection uses SSL/TLS encryption, which sounds reassuring until you realize the entire system hinges on just two things: your Google password and a PIN you probably made too simple.
If either gets compromised through phishing or those increasingly sophisticated “tech support” calls your relatives keep falling for, an attacker gains god-mode access to your machine. Recent data shows social engineering attacks targeting remote access tools have surged alongside remote work adoption, making this vulnerability particularly relevant for today’s distributed workforce. Social engineering attacks result in data exposure in 60 % of cases—16 points more than other initial access vectors.
The Real Dangers You’re Missing
Full system takeover is just one social engineering call away. In 2025, 91 % of cyber attacks begin with a phishing email.
Here’s the nightmare scenario playing out daily: Someone claiming to be from “Microsoft support” convinces you to install Chrome Remote Desktop for “urgent security updates.” Within minutes, they’re rifling through your files, accessing your banking, and potentially installing keyloggers for future harvests. Unlike business tools like TeamViewer with session-specific codes and advanced authentication, Chrome Remote Desktop offers no such protection.
The software also struggles with third-party firewalls, potentially leaving network ports exposed like an unlocked door. This creates additional attack vectors beyond the primary Google account vulnerability, especially problematic for users on public Wi-Fi networks, where password managers face additional risks.
How to Lock Down Your System
Three critical steps to eliminate unwanted remote access.
Start with a digital inventory. Open your computer’s installed programs list and ruthlessly delete any remote access software you don’t actively use—Chrome Remote Desktop, TeamViewer, AnyDesk, the works. Next, audit your firewall rules for exceptions you don’t recognize, especially around common remote desktop ports.
Finally, if you must keep remote access tools, strengthen your defenses:
- Enable two-factor authentication on your Google account
- Create a genuinely complex PIN (not your birthday)
- Always use a VPN when connecting remotely
For users requiring regular remote access, consider enterprise-grade alternatives like Microsoft Remote Desktop or business versions of TeamViewer that offer additional security layers. Your future self will thank you when the next wave of remote access scams hits.